Resources
Understanding Role Delegations in Oracle ERP/HCM Cloud
Fraud and Data Loss - one and the same?
Securing the Financial Close
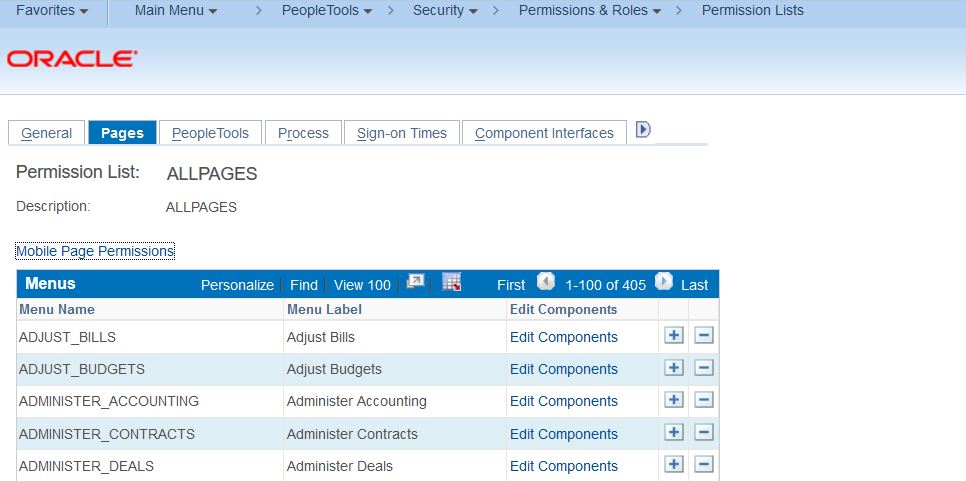
PeopleSoft customers often utilize the Users: PS or VP1 for system maintenance and configuration. These accounts in our research are often granted ALLPAGES access - effectively giving access to the whole Application.
The problem is that these accounts don't need all of this access, all of the time.
These generic accounts are given to Power Users, administrators to manage the Application and/or diagnose and fix issues. The issue is that they have this access when there are no problems, and they are not tied to a human being
Having a generic UserID that can only restart the Batch server for example is far less of a risk than a User who can do practically anything in your Application.
Do we truly need to give these accounts access to everything all of the time? Is there some trade-off between time and security that we can live with?
From our experience one of the added pressures to resolving these access issues is the stance of Auditors. Where Generic Accounts are used the idea is just to simply note that these Users exist.
The problem is that these Users usually have vast knowledge of the Application, it's configuration and the transactions that run through it.
To that degree, the ongoing audit position is one of ignorance to these Users. In fact, we have seen time and time again that ongoing audit review of access involves leaving these Users out of the analysis altogether.
We contend that these Users should be left in, the access to these accounts by Employees documented and monitored for changes.
A common-sense principle and will help to create a degree of accountability, especially if you have auditing switched on Security changes. Rather than using VP1, or PS, each User has a named account.
By securing transaction approvals to a select number of people you can be sure that when it comes to actually finalizing transactions the chosen Users are the ones completing them. For reporting you now make sure that these generic, Power Users do not have access to Workflow Approval Roles.
By having an Environment that regularly represents Production, issues can easily be reproduced, thus reducing the need for these Power Users in Production.
Access removal can come in the form of locking the accounts, or removing Roles except the ability to grant itself Roles (that in turn would provide access to the functionality required for the support issue) via the Security pages in the Application. Now when an issue arises again, we would turn to a ticketing system to raise the issue, what security was required to do the job, and that at the end it was removed again. It is very beneficial with this strategy to have auditing switched on Security, or the functionality that grants Roles to Users. This auditing serves as proof that what was required in the ticket was granted, that it was removed and that these accounts are not being granted access to things outside of these support requests.
This solution involves spending money, and has wider ranging implications on your Business Processes. Identity Management solutions provide a blanket around the User Provisioning, several solutions allow for emergency access or break glass access to be granted and tracked. This essentially automates the process of managing access, depending on configuration.
For more information about our Services for PeopleSoft click here.
Fraud and Data Loss - one and the same?
Securing the Financial Close